When a Linux partition is encrypted, access to the partition’s stored data and storage space is inapplicable to users who do not have the right access/authorization. The same Linux partition can only be termed as decrypted if direct access to it is authorized.
The authorization/decryption phase requires the user accessing the locked partition to provide a matching encryption key used to lock access to it.
Benefits in Encrypting a Partition in Linux?
A lot of benefits are associated with encrypting a Linux partition.
For users using the Linux operating system for commercial or business purposes, data confidentiality is retained in case of a system breach. Encryption mechanisms implement ciphertext techniques to store data making it impossible for unauthorized users to decipher stored data without an encryption key.
Encryption reduces Cybersecurity budgets. Just because a system’s firewall is breached does not imply that the system’s data has to be compromised. Impenetrable data helps sustain a system’s integrity.
This article will walk us through a good approach for encrypting and decrypting a partition in Linux.
How to Encrypt and Decrypt Linux Partitions Using Cryptsetup Tool
This partition encryption and decryption tool draw its functional implementation from DM-Crypt (the Linux kernel use it as an encryption subsystem). Cryptsetup encryption and decryption mechanism is not only limited to disk partitions but also user files and removable media like flash disks.
LUKS or Linux Unified Key Setup is the standard utilized by Cryptsetup. This standard is associated with disk encryption specifications which ensure its functional compatibility on different Linux OS distributions.
Install Cryptsetup in Linux
Reference the following guide for the installation of Cryptsetup encryption and decryption utility on various Linux operating system distributions.
$ sudo apt install cryptsetup [On Debian, Ubuntu and Mint] $ sudo yum install cryptsetup [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-fs/cryptsetup [On Gentoo Linux] $ sudo pacman -S cryptsetup [On Arch Linux] $ sudo zypper install cryptsetup [On OpenSUSE]
Once the Cryptsetup installation process successfully completes, we can make sure it is installed on our Linux systems by confirming the installed version.
$ cryptsetup --version cryptsetup 2.4.3
Encrypt Linux Partition
The first step is to prepare our targeted partition for encryption. The disk drive that we want to encrypt should be attached to our machine. We can use the lsblk command to list them.
$ lsblk
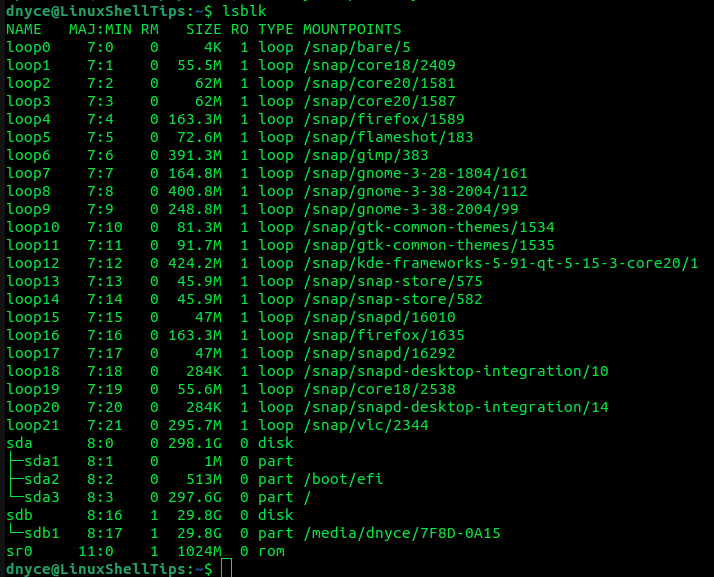
We are interested in the listings of column TYPE labeled part. For this tutorial exercise, we will be using the sdb1 partition listed in the above screen capture. Make sure you backup the data of the partition you wish to encrypt since we will need to format it.
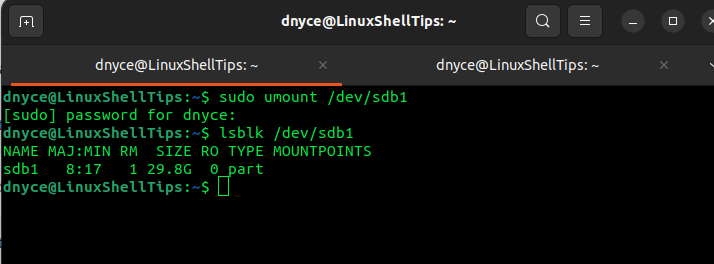
When dealing with removable media, you will need to first unmount it.
$ sudo umount /dev/sdb1
The lsblk command should then confirm that the partition was successfully unmounted.
$ lsblk /dev/sdb1
The following cryptsetup command will format our targeted partition and in turn create a LUKS encryption container.
$ sudo cryptsetup luksFormat --type luks1 /dev/sdb1
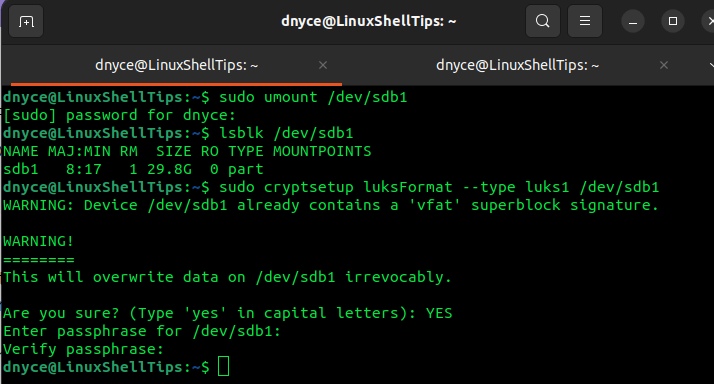
You will be asked to provide and confirm a passphrase for encrypting the partition.
Accessing [Decrypting] an Encrypted Partition in Linux
For removable media, remember to eject it and re-attach it before proceeding with the article.
The above LUKS formatted partition is not directly accessible. We need to create a mapper for it:
$ cryptsetup -v luksOpen /dev/sdb1 my_drive_mapper
Enter the passphrase you created earlier when prompted:
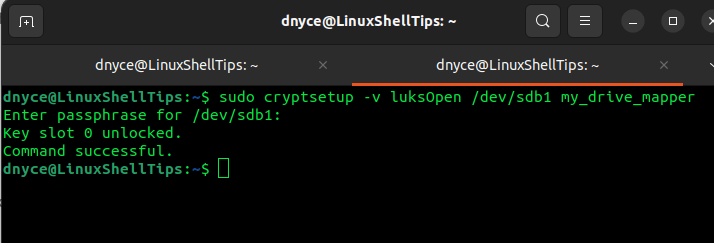
We have named the partition mapper my_drive_mapper.
To view the created mapper inside the /dev/mapper directory, we will use the command:
$ ls -l /dev/mapper
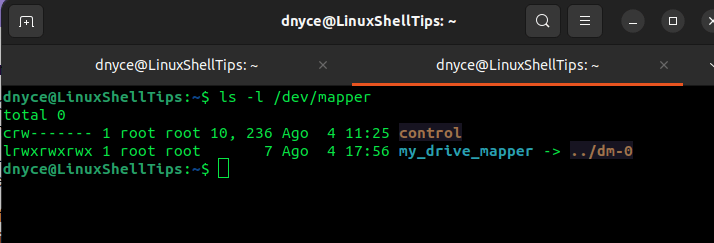
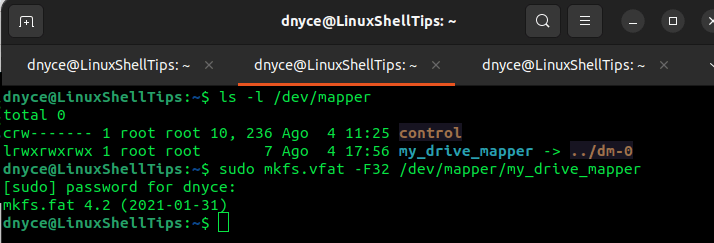
As you might have noticed, our partition is not associated with any filesystem, we can create one with the Linux mkfs command:
$ mkfs.vfat -F32 /dev/mapper/my_drive_mapper
Create a mounting point/directory for this mapper and mount it.
$ sudo mkdir -p /mnt/encrypted $ sudo mount /dev/mapper/my_drive_mapper /mnt/encrypted
We can now copy data to our encrypted partition from the mount point.
We can use the lsblk command to confirm the mapper type.
$ lsblk | grep my_drive_mapper
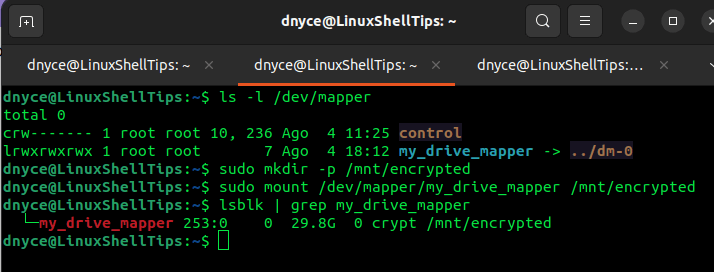
To unmount the partition after use, we will need to unmount the mapper.
$ sudo umount /dev/mapper/my_drive_mapper
To close the partition volume and disassociate the kernel memory from the mapping and the key, implement the command.
$ sudo cryptsetup luksClose my_drive_mapper
We have successfully covered how to encrypt a Linux partition and how to decrypt it in order to write data into it. Know of other cool ways of encrypting a Linux partition? Feel free to leave a comment or feedback.
