SSH or Secure Shell Protocol has earned its name as a secure, reputable, and reliable cryptographic network protocol, which is used to access remote machines and servers over unsecured networks.
The primary purpose/features of SSH can therefore be summarized as a secure connection and remote access. When you have a remote machine or server custom configured to your preferences e.g. file-sharing or download, it is sometimes important for the authenticated and authorized SSH users that are accessing your remote system to abide by certain rules and regulations.
For instance, maybe you do not want the SSH users to navigate to other directory or folder locations on your system. To achieve this objective, you can limit the number of commands such users are required to execute once they have successfully accessed the remote Linux machine/server.
This article will focus on how to restrict SSH users from executing certain commands once they successfully log in to a remote Linux machine/server.
Install OpenSSH in Linux
Please note that SSH is a network connection and access protocol. In order to use it, we need the aid of an application package that supports its usage. Install OpenSSH on both local and remote Linux machines through the following installation reference for different Linux OS distributions.
$ sudo apt install openssh-server [On Debian, Ubuntu and Mint] $ sudo yum install openssh [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a net-misc/openssh [On Gentoo Linux] $ sudo pacman -S openssh [On Arch Linux] $ sudo zypper install openssh [On OpenSUSE]
Restrict Commands for SSH Users in Linux
With OpenSSH installed on both remote and local Linux machines, the next step is to configure SSH key-based authentication. On the local machine, generate an SSH key pair with the following command:
$ ssh-keygen
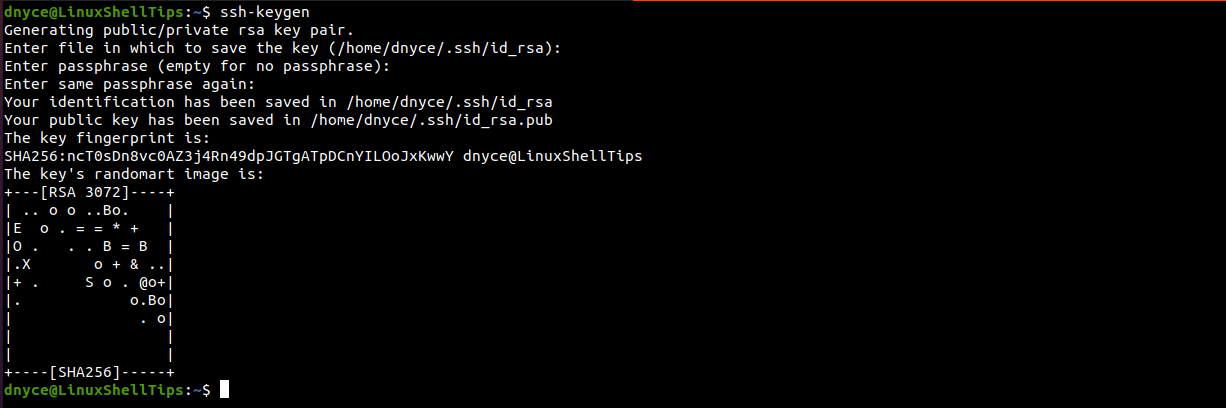
From the above screen capture, we can see that a public key (/home/dnyce/.ssh/id_rsa.pub) has been generated. We need to copy this public key to the remote server/machine we will be accessing. We will use the ssh-copy-id utility for this task as it comes prepackaged under OpenSSH.
Its syntax is:
$ ssh-copy-id remote_username@remote_host_ip
Its implementation will look like the following:
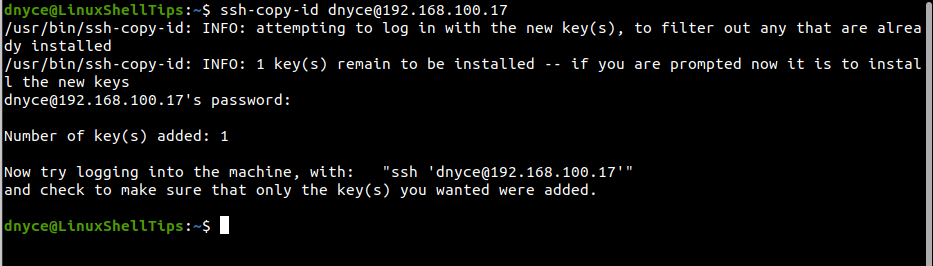
You should now be able to login into the remote server without a password prompt:
$ ssh remote_user@remote_host_ip
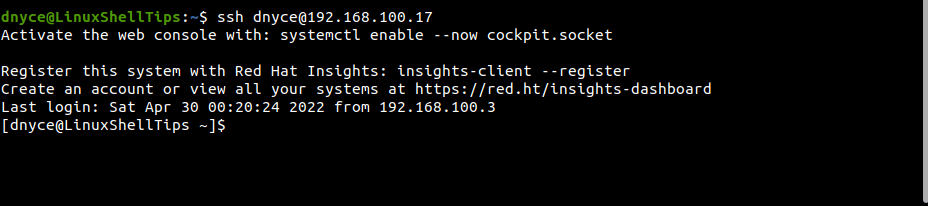
On the remote Linux server/machine, authorized_keys files should be created inside the directory path ~/.ssh. If we open this file, we should see the copied public key that allows this remote machine/server to communicate with our local machine.
$ cd ~/.ssh $ sudo nano authorized_keys
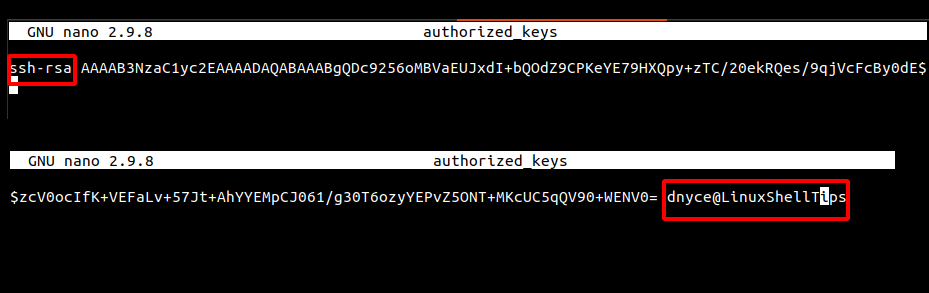
To restrict a user to only use the ls command on this remote server/machine, we can modify this file in the following manner.
from = "192.168.100.3",command="/usr/bin/ls" ssh-rsa AAAAB...+WENV0=dnyce@LinuxShellTips
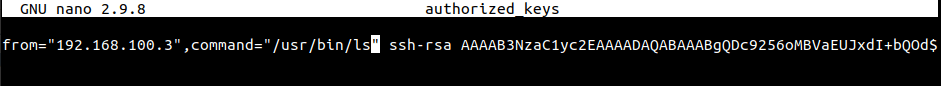
The entry from=”192.168.100.3″ points to the IP address of the local machine and command=”/usr/bin/ls” specifies the only command to be executed.
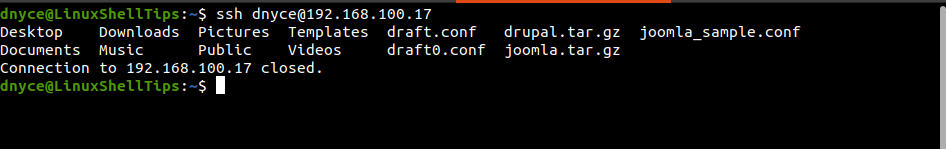
If we exit the server and try to log in again via SSH, the ls command will execute, and the connection to the server will be closed.
$ ssh remote_user@remote_host_ip
Restrict SSH Users to Specific Commands Using Bash Script
With the above method, we are limited to a single command usage (command=”/usr/bin/ls”). To specify multiple limited commands to be run by an SSH user, we could use a bash script created in /usr/local/bin and add its path to the authorized_keys file.
$ sudo nano /usr/local/bin/limited_commands.sh
Add the following lines of code to it.
#!/bin/bash echo "1. ls" echo "2. ping google.com -c 5" echo "3. top" read -p 'Choice: ' choice # Read the choice from user case $choice in 1) ls ;; 2) ping google.com -c 5 ;; 3) top ;; *) exit ;; esac
Make this bash script executable.
$ sudo chmod +x /usr/local/bin/limited_commands.sh
Next, add this file path to the authorized_keys file.
from = "192.168.100.3",command="/usr/local/bin/limited_commands.sh" ssh-rsa AAAAB...+WENV0=dnyce@LinuxShellTips
Let us try re-accessing the server with SSH.
$ ssh [email protected]
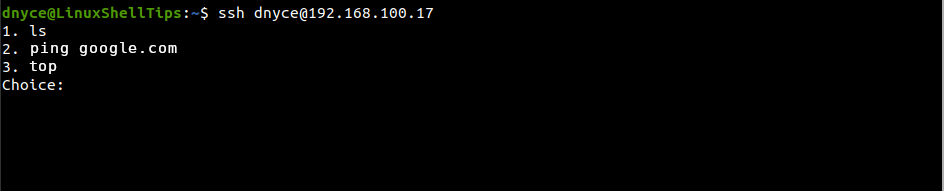
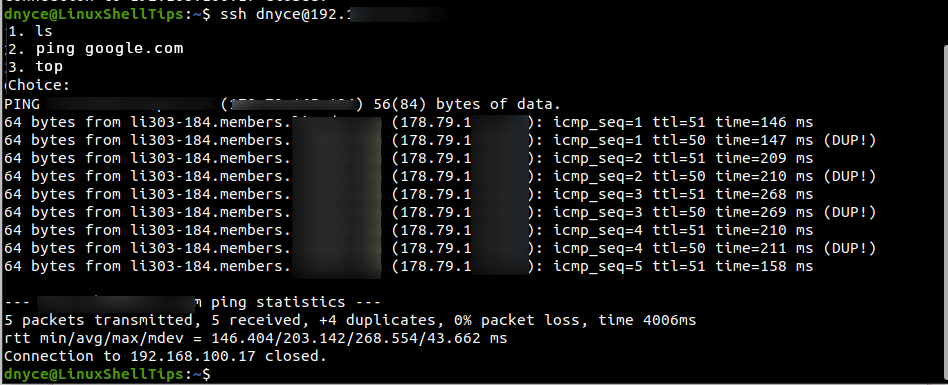
Depending on the limited commands you defined for the SSH user, you can key in a command choice:
We have successfully covered how to restrict SSH users to run limited commands after login on a Linux operating system distribution.

How can we call a program remotely using SSH or SFTP? I am looking for something similar to quote rcmd in FTP.