SSH or Secure Shell program is renowned for its secure operation of network services via a cryptographic network protocol. In most cases, the network interface in use has questionable security hence the need for SSH.
Popular application implementations associated with SSH include:
- remote login
- command-line execution
The basis of SSH applications can be described in the following manner. Firstly, an active and configured client-server architecture needs to pre-exist. Afterward, an SSH client instance is used to make a connection attempt to the targeted SSH server.
An SSH client makes use of the secure shell protocol to initiate a connection with a remote computer. The targeted remote computer needs to have an SSH server installed for it to validate and authenticate the remote connection attempt from the client computer.
This article will walk us through some elite SSH cheats which can be useful in your day-to-day client-to-server/remote machine connection and communication.
SSH Basic Usage in Linux
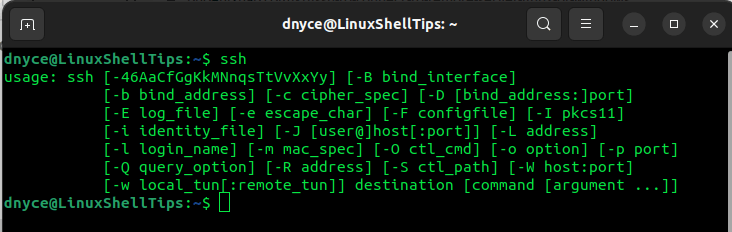
Quick manual access to the use of SSH can be accessed by running the following command on your Linux terminal:
$ ssh
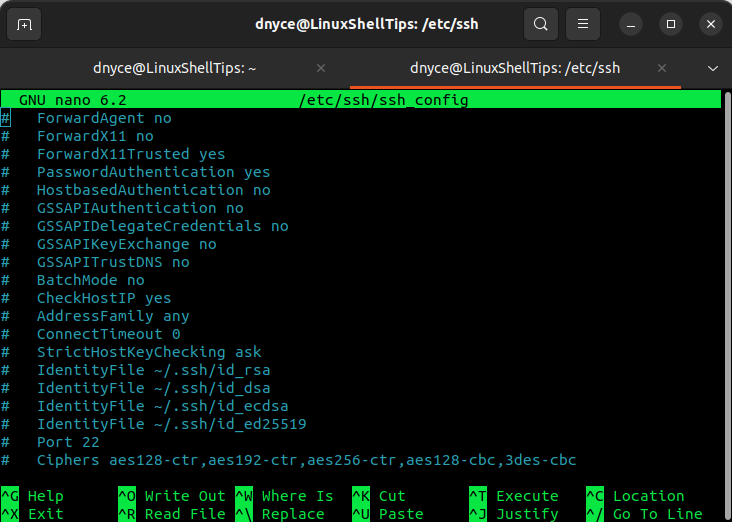
To edit your SSH configurations like access port and connection timeout, you will need to access the configuration file /etc/ssh/ssh_config or /etc/ssh/sshd_config.
$ sudo nano /etc/ssh/ssh_config OR $ sudo vim /etc/ssh/sshd_config
To access a remote/server machine from a client machine via SSH, you will need to adhere to the following command implementation:
$ ssh username@remote_ip_address
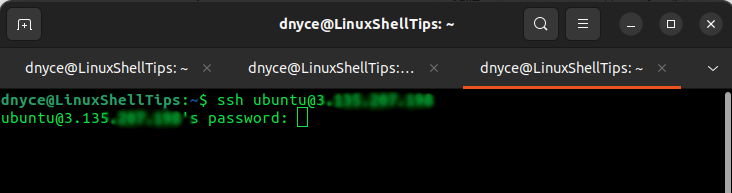
You will then be prompted for a password associated with the remote machine’s user before gaining access.
Useful SSH Cheat Sheet for Linux
Other than gaining direct access to a remote machine and editing the SSH configuration file to your preference, the following SSH cheats have been proven to be very useful in your client-to-remote machine communication.
Generate SSH-Keygen
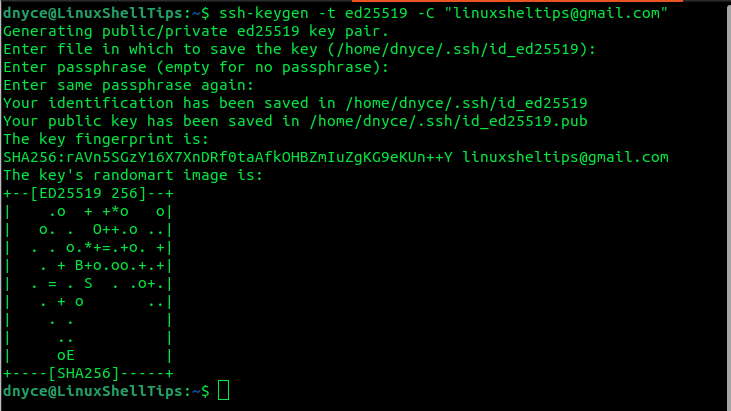
It is a recommendation to make use of the ed25519 algorithm while generating SSH keys. Consider the implementation below using a random email address:
$ ssh-keygen -t ed25519 -C "[email protected]"
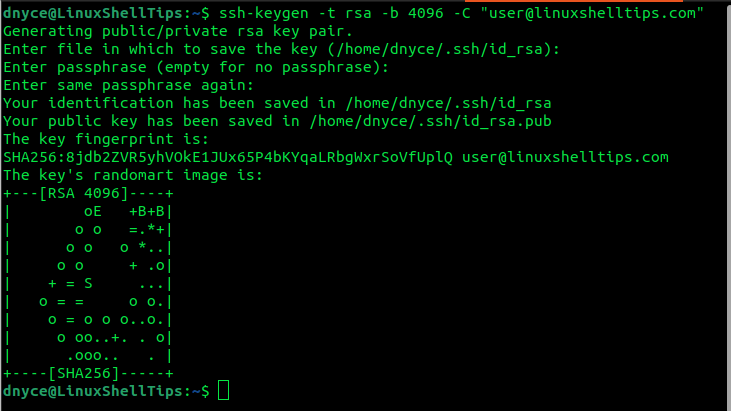
For compatibility reasons, you might decide to generate the key via RSA as demonstrated below:
$ ssh-keygen -t rsa -b 4096 -C "[email protected]"
The -C flag associates each public key with a comment making it easy to link an email address to its rightful public key. During SSH key generation, always remember to associate each private key with a passphrase for security purposes.
Connect Server Using SSH Keys
To connect to a remote machine via a specific private key, refer to the following command implementation:
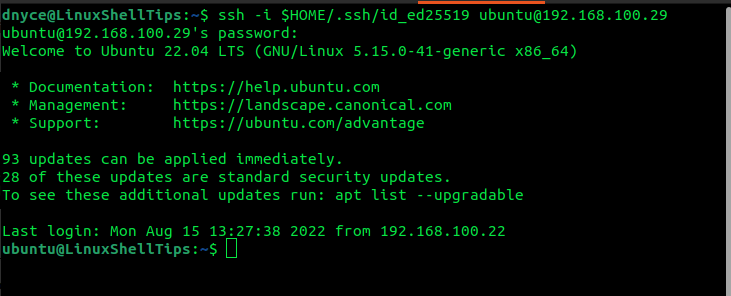
For ed25519 algorithm generated private keys:
$ ssh -i $HOME/.ssh/id_ed25519 [email protected]
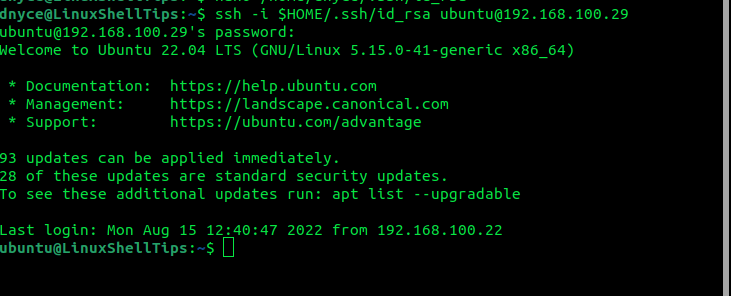
For RSA-generated private keys:
$ ssh -i $HOME/.ssh/id_rsa [email protected]
Connect Server Using Authorized Keys
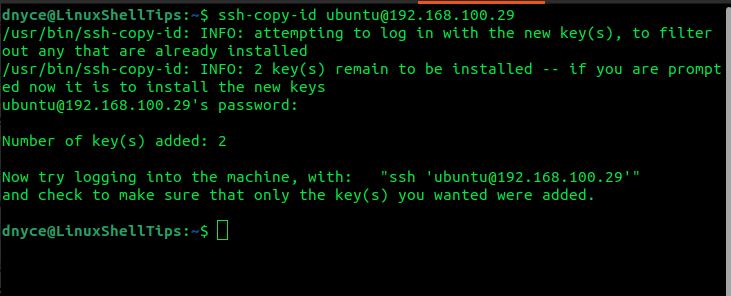
If you aim to use your SSH keys (public keys) with a server system or service like Github, you will need to append a copy of the keys with the file ~/.ssh/authorized_keys on the remote/server system as demonstrated below.
$ cat ~/.ssh/id_rsa.pub | ssh [email protected] "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys"
Alternatively, the following command also works:
$ ssh-copy-id [email protected]
From here, we can connect to the remote machine without being prompted for a password:
$ ssh [email protected]
SCP Commands for Upload/Download Files
When wanting to perform file uploads on remote machines:
$ scp simple.txt [email protected]:/home/ubuntu/Downloads
When wanting to perform recursive local folder/directory upload to a remote machine:
$ scp -rp mypackage [email protected]:/home/ubuntu/Downloads
Downloading/retrieving a file from a remote machine:
$ scp [email protected]:/home/ubuntu/Downloads/simple.txt /home/dnyce/Downloads
Downloading/retrieving a folder/directory recursively from a remote machine:
$ scp -rp [email protected]:/home/ubuntu/Downloads/mypackage /home/dnyce/Downloads
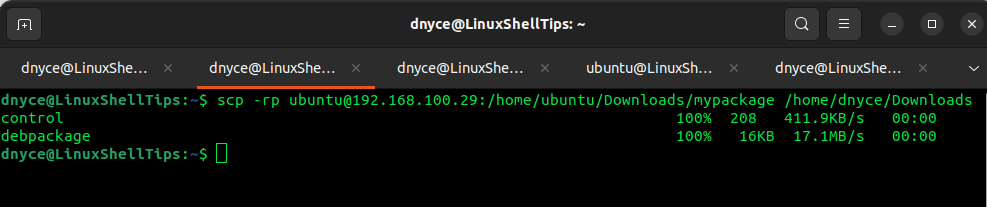
Using Non-Standard SSH Ports
If the SSH server is running on a non-standard port like 3333, your connection should be implemented in the following manner:
$ ssh -p 3333 [email protected]
Running Commands on Remote Machines
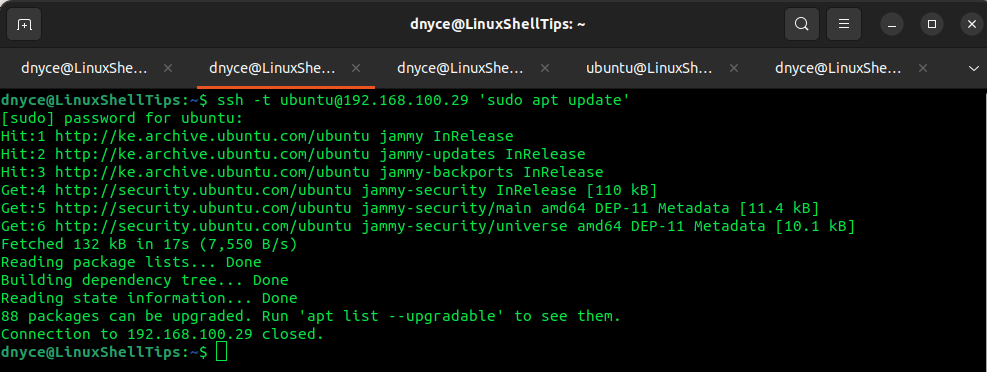
If we want to execute a command on the remote machine like a system update or ping command after a successful SSH connection, we will implement the following command:
$ ssh -t [email protected] 'sudo apt update'
Because we are executing a sudo-privileged command, you will be asked for a user password.
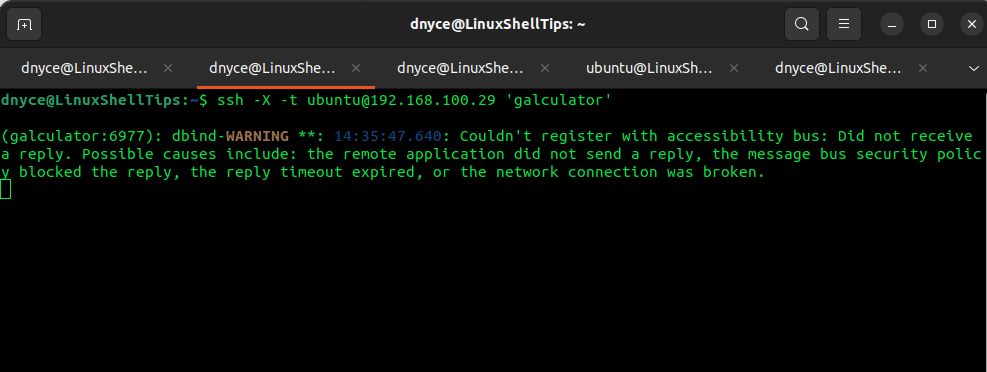
Start Application on Remote Machine
To launch an application like the galculator app after a successful ssh connection, implement:
$ ssh -X -t [email protected] 'galculator'
Manage SSH Keys with SSH-Agent
An ssh-agent is somewhat an SSH key manager that uses a process memory store generated ssh keys making it possible for user access to remote machines/servers without the need for a key passphrase for server authentication.
Simply implement the following command with a running openSSH:
$ ssh-add /path/to/private/key/file
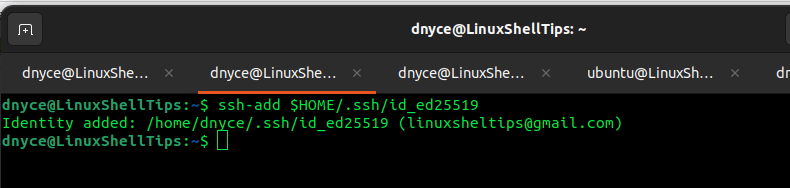
For ed25519 algorithm generated private keys:
$ ssh-add $HOME/.ssh/id_ed25519
For RSA-generated private keys:
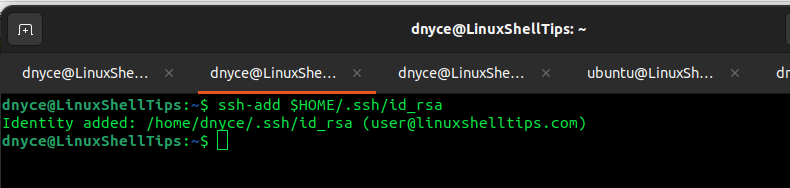
$ ssh-add $HOME/.ssh/id_rsa
Creating SSH Config
Creating the ~/.ssh/config file lets you manage SSH hosts easily. Sample entries in this file look like the following:
Host linuxshelltips* User dnyce UdentifyFile ~/.ssh/linuxshelltips.pem Host linuxshelltips-tutorials Hostname 192.168.100.29 Host api.ubuntumint.com User ravi IdentityFile ~/.ssh/ravi.key
Exit Dead SSH Sessions
If the SSH session is unresponsive, use the following keyboard key combinations.
$ [Enter], ~, .
Multiple Github Keypairs
When working with different Github private repos, with different SSH keypairs, and wish to clone them, consider the following implementation on the ~/.ssh/config file.
Host github-linuxshelltips-tutorials.org Hostname github.com IdentityFile ~/.ssh/id_tutorials Host github-linuxshelltips-nginx-series.org Hostname github.com IdentityFile ~/.ssh/id_nginx
We now have the option of cloning from github-linuxshelltips-tutorials.org or github-linuxshelltips-nginx-series.org in the following manner:
$ git clone [email protected]:linuxshelltips/buildpipelines.git or $ git clone [email protected]:linuxshelltips/buildpipelines.git
SSH Tunnels
This approach is recommended when accessing remote machines invisible to the outside world like the Amazon RDS database:
$ ssh ubuntu@jumphost -N -f -L localport:targethost:targetport
Know of any other useful SSH cheat? Feel free to leave a comment or feedback.
Credit: marcobehler

Hello
I would add the reverse tunnel with
-Rand explain case usages.Thank you for this article. It was really nice summary of ssh usage. All in one place!
Also worth mentioning is ssh-agent forwarding to use your local ssh keys to connect (to git server for example) on the remote machine you ssh into. It saves copying the private key, so it is more secure and convenient. It’s also fairly simple.
You forgot to redirect ports, for example, to access the database behind the firewall.